

Terraform's simple syntax, ease of use, and strong provider support have made it popular among DevOps teams and infrastructure engineers. In this blog, we will discuss best practices you should follow for writing clean, scalable and efficient Terraform code, focusing on:
- Consistent structure and naming convention
- State management
- Infrastructure automation
- Security and compliance
- IaC reusability and templating
We'll also provide some examples of how env0 can help align to these best practices to optimize your Terraform workflows.
Naming convention and folder structure
Debugging issues due to poor structuring and naming conventions can be a pain. You can avoid such problems by adopting a consistent naming convention for your Terraform configuration files, for instance by using underscores (_) in names.
Here are some best practices that will help you maintain readable, manageable, and scalable Infrastructure-as-Code.
- Use short descriptive names to clearly describe the purpose of the resource, making it readable in outputs or error messages.
- Avoid sensitive information in resource names, such as company secrets or personally identifiable information (e.g., [.code]ec2_instance[.code]), and ensure consistent naming conventions to maintain manageable infrastructure.
- Stick to lowercase letters to avoid issues with case sensitivity in different operating systems or platforms (e.g., [.code]ec2[.code]).
- Use underscores (_) over dashes (-) as name separators. Some providers’ resources may not accept dashes - plus, it allows for easy refactoring (e.g., [.code]ec2_instance_1[.code]).
- Include the environment in the name to avoid conflicts when managing resources across multiple environments (like production, staging, and development), and enhance clarity (e.g., [.code]prod_database_instance).[.code]).
- Standardize a structure and agree on naming conventions on an organizational level to maintain consistency. A common pattern might be <environment>_<application>_<resourceType>_<name> (e.g., [.code]prod_app_webserver_01[.code]).
- Employ reusable variables to make your code more maintainable. In Terraform, you can define your variables in a.tf file and use them from there.
Another thing to consider are the Terraform configuration files and folder structures. Effectively organizing Terraform those can help you maintain scalability, readability, and ease of management, especially as your infrastructure grows.
Here are some best practices for structuring your Terraform projects:
- Keep your main configuration .tf files (root module) in the root of your project directory.
- Use separate directories for each environment (e.g., prod/, stage/, dev/) with a consistent naming convention. Each directory can have its version of main.tf, variables.tf, outputs.tf, etc., pointing to the appropriate modules.
- Include a README.md in your root directory and each module directory, explaining the project or module's purpose, usage, and any prerequisites.
- Implement file organization to isolate components needed for your Terraform code, such as variables.tf, outputs.tf, providers.tf, terraform.tf – depending on your needs, for easy management.
How env0 can help
With env0, you can manage multiple environments without duplicating your files, saving you valuable time and effort. This environment structure can reflect the way your files and folders are organized in Git.
For example, one thing you can do is create a project in env0, and set up environments for development, testing, and production. Each of these will link to the same directory, but you can give them their specific settings, like [.code]bucket_name[.code].
Visit env0 docs to learn more about Environments and this guide to learn about Environment Discovery. (also covered below)
On the standardization side of things, env0 also provides several features to help with rolling out and maintaining consistent naming conventions.
One of these is Shared Variables, which allows you to create a hub for your variables in project settings, listing your options in a user-friendly drop-down feature.
This ensures the entire team stays on the same page and follows the extract the same standardized naming convention.
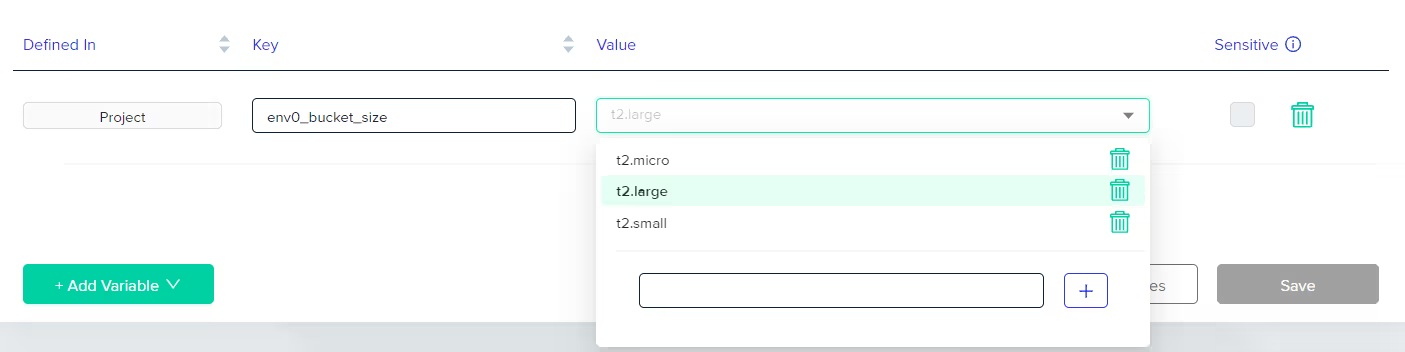
Visit env0 docs to learn more about Variables Management.
State Management
Properly managing your state files can help you avoid misconfiguration or production issues.
Apply these best practices to help manage Terraform state:
- Store Terraform state files in a centralized location like AWS S3 or Azure Blob Storage to avoid local state conflicts and ensure restricted access across your team.
- Avoid storing state files in any version control system (VCS) repositories to prevent exposing secret credentials as plain text.
- Enable state locking in your backend to manage Terraform state, prevent concurrent state modifications, and ensure your changes are applied sequentially.
- Schedule regular backups of your state files to ensure quick recovery from data loss or corruption.
- Consider using separate state files for bigger projects to reduce complexity. Otherwise, you might run into problems like managing dependencies between resources and risking state corruption.
How env0 can help
env0 simplifies managing your infrastructure's state with features like environment locking, drift detection, and ad-hoc task management.
With these features, there's no need to manually set up locks, S3 buckets, or other configurations, enabling you to manage your infrastructure easily.
Environment Locking feature in env0 lets you track all versions of your state files by setting up a remote state backend, allowing the use of the same state file across environments to keep them organized and to avoid state file clashes.

Visit env0 docs to learn more about Environment Locking.
Drift Detection gives you better control over your infrastructure. This feature in env0 helps you monitor and catch unintended changes early, informing you about any discrepancies in your setup so you can fix them before they become problems.

When a drift detection job is executed, you'll see its status under the Deployments tab.

Check out this guide for more information about Drift Detection.
Ad-hoc tasks in env0 provide a central hub for executing ad-hoc commands like [.code]terraform state mv[.code] and [.code]terraform import[.code], enabling team members to run tasks centrally as needed without risking infrastructure stability.
In a typical scenario, you would have to run these ad-hoc commands on your local system, making it hard to track who did what.
Visit env0 docs to learn more about Ad-hoc tasks.
Infrastructure Automation
By automating infrastructure, Terraform creates opportunities to minimize errors and speed up rollouts. This will reduce manual tasks and ensure that changes to the infrastructure are traceable, repeatable, and reversible.
Here are some best practices to follow while automating your infrastructure.
- Use a version control system (like Git) to automate the provisioning, and de-provisioning of your infrastructure and maintain the application lifecycle. This lets you track changes, collaborate effectively, and roll back when needed, keeping a consistent infrastructure state acting as the Single Source of Truth (SSoT).
- Design automation scripts and configurations to be idempotent. Running them multiple times on the same system should produce the same result, improving reliability and error handling.
- Test, validate, and plan your infrastructure code using your automation pipelines or scripts before applying the changes by creating a pull request. Keep your environments (test, non-prod, etc.) similar to each other.
- Schedule your infrastructure deployments and destroy unused resources using automation to prevent manual intervention, which can disturb the infrastructure state.
How env0 can help
env0 offers features like environment discovery capabilities that automatically create and destroy environments based on pull requests. This enables you to stay within the GitOps flow and maintain Git as your main source of truth for code management, auditability, etc.
This also enables teams to test new features in isolated environments without manual intervention, reducing operational overhead.

Check out this guide for more information about Environment Discovery.
With env0, you can also set custom TTL policies to automatically destroy environments after a specified period to maintain clean infrastructure. Visit env0 docs to learn more about TTL Policies.

Additionally, you can schedule environment provisioning and de-provisioning to align with business hours or project needs, further optimizing resource usage.

Visit env0 docs to learn more about Scheduling.
For OpenTofu users, env0 provides CI testing to automate module testing in the private registry. This allows you to ensure your modules are validated and function as expected before deployment.

Check out this guide for more information about Modules CI Testing.
Security and Compliance
Detecting vulnerabilities early is key to creating a secure and compliant system. Every one of your team members must follow the appropriate automated security and compliance checks to ensure the security of the infrastructure and meet the organization’s standards. Implement these best practices to ensure your system is secure and compliant.
- Implement Role-Based Access Control (RBAC) to ensure users have the appropriate permissions to execute tasks that align with their roles and responsibilities.
- Maintain detailed audit logs of user activities to track changes, access, and system events for accountability and compliance purposes.
- Use tools like Checkov or OPA to ensure that the infrastructure is thoroughly scanned for vulnerabilities before executing [.code]terraform apply[.code].
How env0 can help
Custom Role-Based Access Control (RBAC) roles come as default in env0, which mean you can assign permissions to individual users based on their roles and responsibilities.

The project’s admin can view detailed audit logs in env0 to track team activity and monitor all activities around the infrastructure without any special configuration. Audit logs in env0 would provide the following information:

Visit env0 docs to learn more about RBAC roles and audit logs.
env0 also allows you to integrate the Checkov plugin into your env0 deployments to scan your Terraform code for vulnerabilities and ensure adherence to best practices. The plugin will install and execute the Checkov binary.
Moreover, you can use native OPA (Open Policy Agent) integration to add approval flows within your env0 deployments to implement granular security and compliance policies.
These are just a few examples. Click here to learn more about evn0 Plugins.
IaC Reusability and Templating
Implementing reusability and templating can increase efficiency by allowing teams to use parameterized templates and modular components.
Here are some best practices for implementing these capabilities in your Infrastructure-as-Code:
- Apply modularization by breaking your configuration into reusable modules, functions, or classes. While doing so, use a descriptive, consistent naming convention across your organization.
- Use the parameterization technique in your IaC code to increase reusability across different environments and configurations.
- Implement shared variables to maintain consistency and provide reusability across teams.
- Create template repositories with predefined IaC templates for frequently used configurations.
- Ensure that modules and templates are environment-agnostic to work across different environments without modification, relying on parameterization.
How env0 can help
In addition to the previously mentioned reusable variables, env0 also provides you with the option to manage a shared private modular registry, where teams can easily exchange modular components.
This maintains uniformity across various projects and environments, facilitating the secure sharing and reuse of these modules within your organization.

Visit env0 docs to learn more about Modular Registry.
Additionally, the env0 also enables template reuse, allowing you to create shared templates based on your specific IAC framework, version, and other configurations by attaching your template repository.
Using these, you and your team can create new environments without duplicating work or creating new configurations.

Visit env0 docs to learn more about Templates.
Conclusion
We have explored many of Terraform's best practices, their value to your project, and their long-term benefits in your infrastructure development.
However, these are not the universal guidelines and our suggestions here may or may not work, depending on the nature of your project, its size, and other requirements.
This is exactly where env0 comes in – a flexible tool that lets you apply the things that could help and skip those that won’t, while always reducing your workload.
By combining collaboration options with governance capabilities, it allows you to pave the ‘golden path’ that makes sense for you in a quick, user-friendly manner.
Frequently Asked Questions
Q: What is the best practice for storing a project's Terraform state file?
The best practice for storing a project's Terraform state file is to use a remote backend, such as AWS S3, Google Cloud Storage, or Terraform Cloud. This ensures state consistency, supports collaboration, and provides secure access and versioning.
Q: How does env0 help with Terraform state management?
env0 simplifies state management by providing a secure, remote backend with versioning, environment locking, and drift detection capabilities.
Q: What role does env0 play in managing multiple Terraform environments?
env0 offers features like environment discovery and variable reuse, making automatically creating, managing, and destroying various Terraform environments easier.
Q: How can env0 enhance security and compliance in Terraform projects?
env0 integrates with security tools like Checkov, TFlint and OPA and offers RBAC and audit logging to enforce security policies and compliance in Terraform deployments.
Q: How does env0 support IaC reusability and modularity with Terraform?
env0 provides a module registry and predefined templates, enabling teams to manage reusable Terraform modules and simplify infrastructure setup.



.webp)



.png)


.avif)
.png)