What's New with env0
Catch up on latest product updates.

.png)
Blog
video
Video
Drift Cause Analysis: Context That Drives Confident Action
Introducing Drift Cause Analysis from env0—an AI-powered feature that explains why drift happened, so you can resolve it faster and with confidence.

Blog
video
Downloadable
env0 has released 3 key features this month, directly helping new and existing customers. One of our features (Private provider registry) has already been covered in a separate blog—and this month's highlighted feature will be Remote state access control.

Blog
video
Downloadable
Provider Registry
env0’s Provider Registry feature allows users to store Providers in a public or private repository and reference it for use within code. Best of all, you are able to pull different versions of the code with simple changes. When running inside env0 we will even handles the authentication without the need for any additional steps or configuration.

Blog
video
Downloadable
Terraform Modules Guide: Best Practices & Examples
Infrastructure as Code is first and foremost code, and a chief principle of writing good software is leveraging abstractions to make your code reusable, scalable, and consistent. Terraform modules are the abstraction provided by HashiCorp to take logical groupings of resources and package them together in a reusable object.

Blog
video
Downloadable
Which IaC Scanning Tool is the Best?: Comparing Checkov vs tfsec vs Terrascan
In this blog post, we will compare three popular IaC scan tools: Checkov, TFsec, and Terrascan. We will compare them based on their features, performance, usability, and compatibility.

Blog
video
Downloadable
Chris' Corner - April 2023
In the second iteration of Chris’ Corner, we will review the features released in the month of March.

Blog
video
Downloadable
Chris' Corner - March 2023
The env0 team has been busy this year—learn more about our favorite env0 feature releases of 2023 so far, including Environment Locking, Remote Plans, Project Level Custom flows, and more.
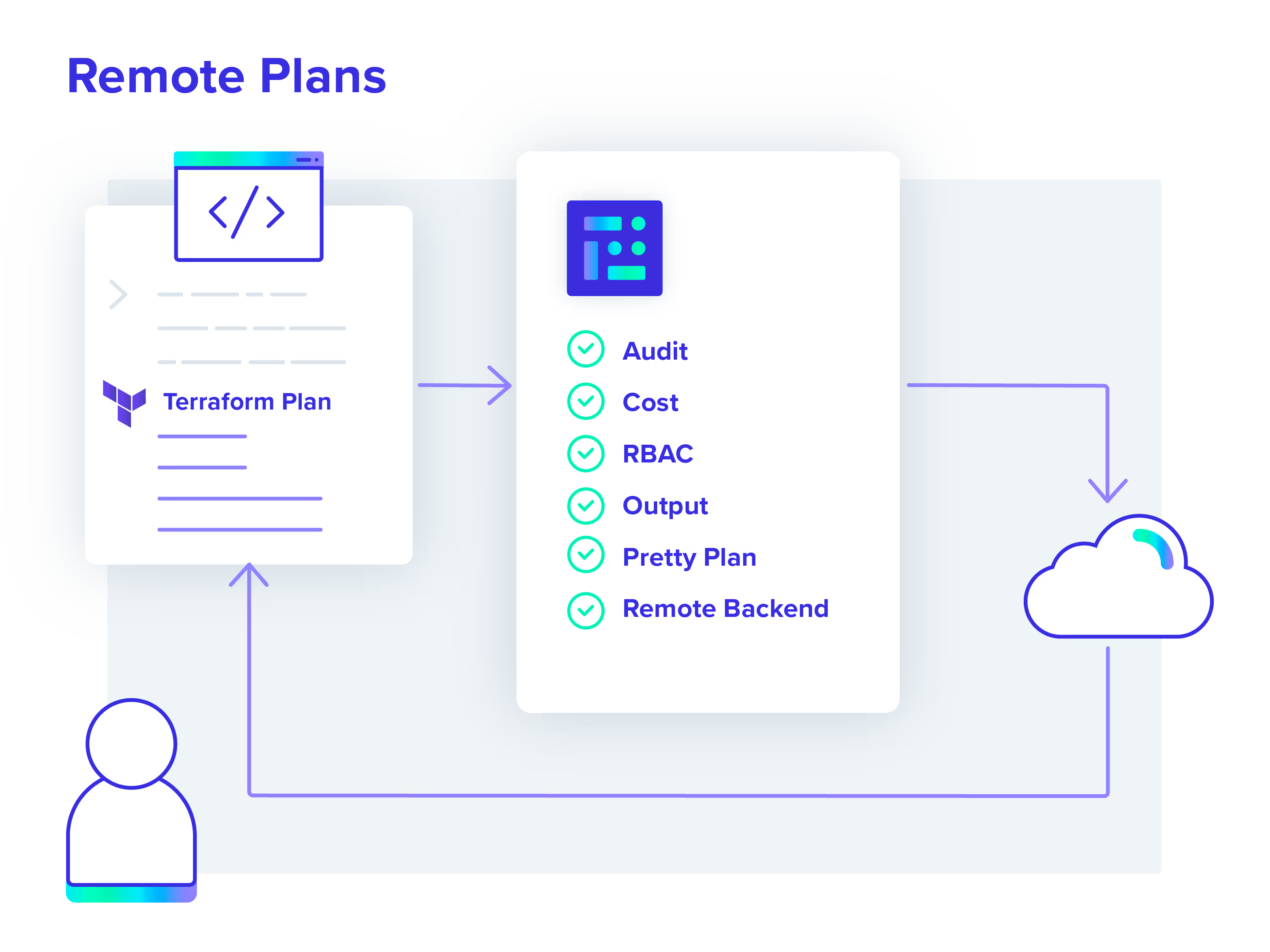
Blog
video
Downloadable
How to use Terraform locally with the env0 platform
Under pressure to use an automated IaC tool but don’t want to deal with the overhead of pushing code for every change? Here’s a step-by-step look at how to use Terraform locally and still have access to all the benefits of the env0 platform.

Blog
video
Downloadable
How to integrate Azure DevOps with env0
Feature Release: env0 has released an integration with Azure DevOps, allowing teams to automate the provisioning and management of cloud resources directly from Azure DevOps. This integration is useful for implementing gitops workflows, providing self-service provisioning for developers, and enforcing governance and compliance controls.

Blog
video
Downloadable
How to Implement fine-grained Role-Based Access Control for Your Infrastructure as Code with Custom RBAC Roles
In a world where infrastructure is constantly changing and evolving, it's more important than ever to have tight controls over who can make what changes. Granular RBAC allows you to give each user only the permissions they need to do their job, nothing more. This reduces the potential attack surface of your infrastructure and helps to prevent breaking changes.

Blog
video
Downloadable
You Need Audit Logs for Your Infrastructure as Code, and They’re Easy to Set Up
In this post we’ll take a look at why auditing is necessary for Infrastructure as Code, the benefits of having an audit trail for Terraform and other IaC frameworks (such as Terragrunt, Pulumi, CloudFormation, Kubernetes, and others), and share how you can automate your audit trail easily with env0.

Blog
video
Downloadable
Manage Terraform Remote State Using Remote Backend
You can now use env0 as your remote backend for Terraform state storage, including migrating your existing remote state from other platforms to env0.

Blog
video
Downloadable
How to make managing multiple Terraform environments easier
How many of you have started with Terraform and discovered you need the same code to build multiple environments? Perhaps a dev, stage, and production environment? After researching Workspaces, Branches, and Terragrunt, you aren’t completely satisfied and want to know if there is another way. If you are here, I’ll assume that’s you!

Blog
video
Downloadable
New: Authenticate With Third-Party Services Using the OpenID Connect Integration
Now you can make your deployments even more secure with OpenID Connect support!

Blog
video
Downloadable
Managing tfvars Files and Terraform Variable Hierarchy
Learn more about Terraform variables, terraform module variables, and ways to DRY out your code with some examples of how to build complex variable hierarchies.

Blog
video
Downloadable
AWS CloudFormation support added
CloudFormation joins Terraform, Terragrunt, Pulumi, and Kubernetes as a core IaC tool supported in env0!

Blog
video
Downloadable
Terragrunt Run-All
Now it's possible to deploy multiple Terraform modules in a single command using 'terragrunt run-all'.

Blog
video
Downloadable
env0 Workflows Get a Power Up
Workflows solve the problem of provisioning complex infrastructure resources that have dependencies, and using multiple frameworks for your infrastructure-as-code.

Blog
video
Downloadable
Ad-hoc tasks
DevOps engineers sometimes need to perform one-off commands on their Terraform code or state. For example, “terraform import” or “terraform state rm”, or any other Terraform or bash commands. The problem is that it is dangerous to allow users to work directly from a terminal.

Blog
video
Downloadable
Managing Pulumi IaC with env0
Manage Pulumi defined infrastructure right next to your other IaC code. In this video, we’ll show you how to integrate your Pulumi code into env0.

Blog
video
Downloadable
Non-Admin API Keys
Generate and maintain role-based access to API keys, providing you the safety of RBAC alongside the convenience of API services.

Blog
video
Downloadable
State File - What is it, and Where Do I Hide It?
If you have deployed anything with an Infrastructure as Code framework (Terraform, Pulumi, etc…) recently, then you have interacted with a state file, and may not have even known it! So, what is the state file? Why is it important? What should you do with it? These are some of the most asked questions when it comes to Infrastructure as Code management. So, let’s get into it!

Blog
video
Downloadable
Time to provide… a Terraform Provider!
Nowadays all is heavy-automated and so, as requested by many of our customers, we now offer a Terraform Provider for the env0 platform! env0 is now extensible with UI, API, CLI, and Terraform Provider.

Blog
video
Downloadable
Multi-Environment Deployment Workflow with env0’s Terraform Provider
Infrastructure is typically built up from multiple layers, starting with the network to the compute layer. In order to deploy your K8s cluster, you typically need your subnets and VPCs defined ahead of time. As I talk to customers about their IaC deployment challenges, I often get asked how env0 can help with orchestrating dependencies amongst these multi-tiered, multi-layered infrastructure deployments.

Blog
video
Downloadable
Automated Drift Detection
env0 is enabling the ability to automatically detect drift and make sure real-world resources in the cloud provider are aligned with Infrastructure as Code files, a huge thing for those Infrastructure as Code users world-wide!











